iPhone shocked a terrible vulnerability: more than 500 million users may have been voyeurized by hac
All along, Apple's security has been respected by users, but recently, Apple has been exposed to major security loopholes.
According to foreign media reports, ZecOps, a San Francisco-based cybersecurity company, discovered a vulnerability on iOS devices, and there is evidence thatAt least 6 network security intrusion activities have exploited this vulnerability.
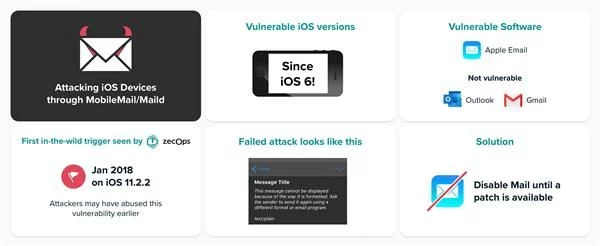
The scary thing is,The vulnerability may affect all versions of iOS 6 and above, and more than 500 million users are at risk of being attacked, and this vulnerability may have been exploited by hackers for eight years.
And this vulnerability does not require any click from the user, as long as an email is sent to the user, even if the email is still in the download process, the vulnerability attack can be triggered.
At present, Apple has acknowledged the existence of this vulnerability, and said it is working hard to fix related vulnerabilities. Apple has fixed security vulnerabilities in the latest iOS 13.4.5 beta. The official version of iOS 13.4.5 should be released publicly in the next few weeks.
The vulnerability has been lurking for eight years, and 500 million users may be attacked
So, how will this vulnerability launch an attack?
According to foreign media, this research shows that the vulnerability can be triggered remotely and has been used by hackers to attack some well-known users.
This vulnerability allows an attacker to use special mail to run remote code by accessing the Mobile Mail and Mailid processes in iOS 12 and iOS 13. A vulnerability could allow an attacker to remotely infect an iOS device by sending an email that consumes a lot of memory.
In other words,Using these vulnerabilities, attackers can leak, modify, and delete user emails.
ZecOps said in its report on Wednesday,They "highly believe" that these vulnerabilities have been exploited by high-level hackers, and the variants of these two vulnerabilities can even be traced back to iOS6 released in 2012, which means that hackers have used them to conduct iPhone and iPad users for up to eight years. Year's attack. If the device is infected, the user does not even know that they are being hacked.
The specific attack route is: the hacker sends a blank email to the victim through the Mail application, causing the latter's system to crash and reset, and the system crash allows the hacker to steal other data such as photos and contact information.
ZecOps claims that even iPhones running on the latest version of iOS can be exploited by hackers to steal their data remotely. The vulnerability could allow hackers to obtain any information that the Mail application has access to, including private messages.
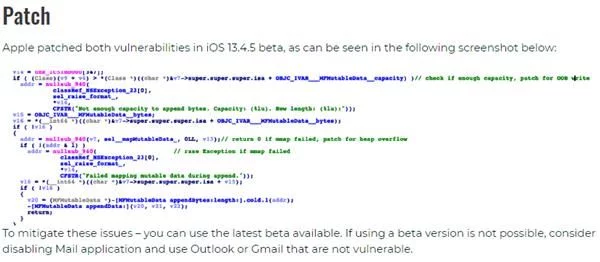
ZecOps found that the reason for this attack is: MFMutableData is in the MIME library and lacks error checking for system calls. ftruncate will lead to transboundary writing.
In addition, they also found a way to trigger OOB-write without waiting for the system call to fail and a heap overflow that can be triggered remotely.
Both OOB-write errors and heap overflow errors occur due to the same problem: the return value of the system call is not handled correctly.
In other words, the vulnerability can be triggered before the entire email is downloaded, even if you do not download the content of the email locally.
What exceptions will occur after the vulnerability is exploited?
Seeing this, some netizens said that I do n’t use email, and I do n’t have rain.
However, the scary part of this vulnerability may not be whether the user uses it, as long as it is in your application list, then you may be the target of the attack.
According to ZecOps research, they found that when your iPhone and iPad are attacked, users should not observe any other abnormal behavior except for the temporary slowdown of the mobile mail application.
In iOS 12, the vulnerability is easier to trigger because the data flow is completed in the same process. As the default mail application (MobileMail), it handles much more resources, which will occupy the allocation of virtual memory space, especially It is the UI rendering, and in iOS 13, MobileMail passes the data stream to the background process, which is maild. It concentrates its resources on analyzing emails, thereby reducing the risk of accidental exhaustion of virtual memory space.
The specific reaction is as follows:
After the attack attempt (success or failure) by the hacker on iOS 12, the user may notice that the Mail application suddenly crashed.
On iOS 13, this attack is not so obvious. Except for a temporary slowdown, no other anomalies will be noticed.
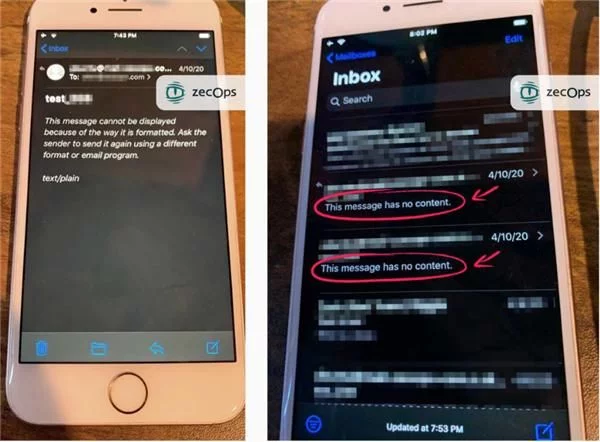
In a failed attack, the email sent by the attacker will display the message: "This message has no content." As shown below:
On iOS 13, an attacker may repeatedly attempt to quietly infect the device without user interaction. On iOS 12, the user is required to click on the newly received email from the attacker to trigger the attack. However, ZecOps also said that it is now certain that MacOS is not vulnerable to these two vulnerabilities.
For its part, these vulnerabilities do not pose too much risk to users-they only allow attackers to read, modify, or delete emails. But if combined with another kernel attack, such as the unpatchable Checkm8 vulnerabilities, these vulnerabilities may allow bad actors to gain root access to specific target devices.
ZecOps found in its report that the targets of hacking are mainly on the equipment of corporate executives and foreign journalists. Therefore, we need not worry too much for now.
How to save yourself?
In fact, in February of this year, ZecOps reported suspicious vulnerabilities to Apple.
On March 31, ZecOps confirmed that the second vulnerability exists in the same area and has the ability to be triggered remotely.
On April 15, Apple released version 13.4.5beta2 of iOS, which contains patches for these vulnerabilities and fixes the two vulnerabilities.
On April 20, ZecOps re-analyzed historical data and found additional evidence, and informed Apple in time that this threat warning must be issued immediately so that organizations can protect themselves because attackers may significantly increase their activity because It has been patched in the beta version.
And Apple has generously acknowledged this vulnerability, so how should we stop this kind of attack before Apple's latest fixed version appears?
ZecOps recommends that users use third-party email apps such as Gmail or Outlook, and disable this original software in the background.
Is Apple's security questioned?
According to official Apple data, about 900 million iPhones are in active use in 2019. Cybersecurity experts believe that its widespread popularity means that serious security breaches, if abused, can cause losses in excess of millions of dollars.
There was Siri wiretapping before, iPhone jailbreak afterwards, and security breaches that are now being exploded. Apple ’s security has also been questioned by users.
One side believes that users believe that any system cannot avoid vulnerabilities. Apple's performance in the past is enough to prove its security, and it still has expectations for Apple.
The other party believes that even Apple has been exposed to security issues, it is time for mobile phone manufacturers to consider counterattack.
What do you think of this? Do you still trust Apple products?